The growth of the Internet of Things (IoT) is unquestionable, with many sources documenting the scale of this with some eye-catching statistics. For example, the Ericsson Mobility Report 2023 states that NB-IoT is forecasted to quadruple by the end of 2028 to around 2 billion devices globally, while 4G and 5G connected IoT devices will grow to over 3 billion by 2028. Bringing this context on to home soil, the IDC Forecast suggests there will be 780 million IoT connections in the UK by 2030.
As mobile data connectivity continues to grow and becomes an integral part of the infrastructure of the country, there is an increasing requirement for organisations to ensure that their data is secure and safe from security breaches. As more and more devices like cameras, vending machines, traffic lights, EV charging stations and dustbins are connected, they open up potential entry points into a customer’s network and are therefore susceptible to attack. IoT security is however an area that is currently being alarmingly overlooked.
According to a report from Palo Alto Networks, 98% of data currently handled by IoT devices and transmitted over the Internet isn’t even encrypted! This is a scary thought and clearly highlights the need for businesses across the UK to safeguard their IoT connections from data hackers, with Research and Markets predicting that the IoT Security Market will grow by 23.1% over the next five years.
So how do we go about keeping all of these connected devices secure? From the device to application server, it is essential to minimise the attack surface from a connectivity perspective.
Basic security steps would be to utilise NAT on a public IP address, or preferably access a private Access Point Name (APN) on the mobile network, with private IP addresses used for connected IoT devices. Virtual Private Networks (VPNs) may then be used over the Internet to connect to an IoT platform or users at other sites for remote management of devices.
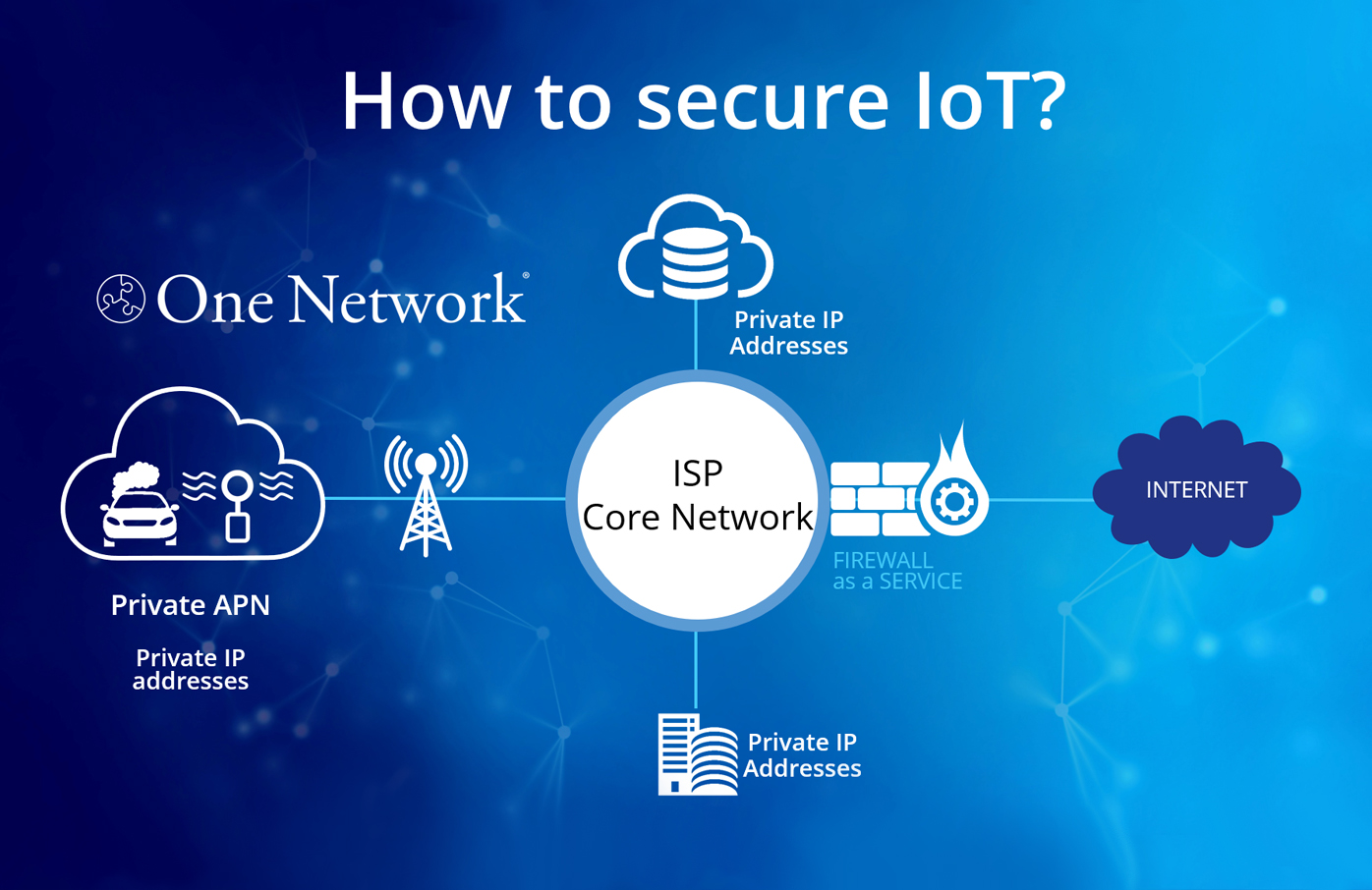
However, why not go one-step further? Connect your IoT devices without the need to traverse the public Internet, so that data traffic is only routable on a private network. This is where Spitfire’s One Network solution comes in…
With One Network, there is no need for encryption, no opportunity for misconfiguration of VPNs or other security policies, nor any potential for attempted attacks via public Internet facing interfaces.
Until now, deploying IoT technology has usually called for multiple connectivity supplier relationships, involved tricky integrations, created the vulnerability of data traversing the Internet, and has not allowed for easy remote management of devices. Spitfire’s One Network changes all of that as it allows you to connect, monitor and manage any size estate of IoT devices, securely and privately, under a single, end-to-end supplier relationship.
If public Internet access really is required, then we can deploy Spitfire’s Firewall as a Service (FWaaS) to monitor and manage policies, to control data flow, provide traffic analysis, and use whitelists to secure remote access into your devices, all through a cloud-hosted deployment to make management far more efficient.
From IoT device to platform, or from users to device, with One Network, data travels over a secure Spitfire controlled private network and the attack surface is completely locked down. One Network truly provides the perfect ecosystem for IoT.
We’re here to help!
Feel free to call or email our team on:
020 7501 3344 or iotsales@spitfire.co.uk
The information submitted on this form will be used solely for the purpose of responding to your enquiry. A copy of our Privacy Policy may be found here
We’re here to help!
Feel free to call or email our team on:
020 7501 3344 or iotsales@spitfire.co.uk
The information submitted on this form will be used solely for the purpose of responding to your enquiry. A copy of our Privacy Policy may be found here
We’re here to help!
Feel free to call or email our team on:
020 7501 3333 or enquiries@spitfire.co.uk
The information submitted on this form will be used solely for the purpose of responding to your enquiry. A copy of our Privacy Policy may be found here